+44 75754 30035 help@rapidassignmenthelp.co.uk
offer
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
The growth of systems reliant on digital systems makes it necessary to employ strong methods to safeguard the operating system and network. As a technology services company, GigaTec-IT has to be extremely concerned with buffer overflow attacks as well as phishing. If these threats are exploited, the company’s operations would be compromised, including the company’s infrastructure and its customer data. Using Wireshark, a widely recognised network protocol analyzer, this report investigates the security landscape of operating systems and networks. Its goal is to evaluate the vulnerabilities in a simulated network environment, propose mitigation strategies on those vulnerabilities and subsequently validate the strategies implemented. In this task, moving on to setting up a prototype network, capturing and analysing traffic, and applying security mechanisms to reinforce the system. Analysis is performed using Wireshark to identify suspicious activities, through testing responses to security threats, and how network problems can be solved. GigaTec IT is hoping that the report's findings will offer it practical recommendations for improving security and maintaining operational integrity. This detailed insight is an excellent resource for students seeking assignment help cheap in 7COM1012 Security of Operating Systems and Networks Assignment Sample writing and understanding.
Operating systems and networking security is critical to its ensuring that unauthorised access, data breaches and service disruptions don’t occur. Programming flaws are exploited by such threats as buffer overflow attacks, allowing malicious code to be inserted, executed, or such errors as a system crash. Phishing attacks do the same thing to users, tricking them into giving up sensitive information, it is a serious threat to business. These threats can be recognised systemically through analysing network traffic and identifying vulnerabilities, thanks to the use of such tools as Wireshark (Einy et al., 2021). Wireshark is a powerful tool for capturing and examining packets sent between or within a network for looking at what’s actually going on. Users can also use this so they know when it becomes suspicious, like if there’s unusual traffic patterns or people attempting to access without warrant. With the tool filtering on the traffic type such as HTTP, TCP and so on, the detection of suspicious activities gets simplified. Wireshark, for example, can find open ports against which an attacker might attack, and malformed packets that might indicate intrusion attempts, or high traffic rates which might indicate a DoS attack (Gao et al., 2021). Network security practises also have legal and ethical implications. In order to maintain compliance with data protection regulation and ethical practises, network testing organisations must put all of these into place. It is protecting user data by packet capture and taking the permission for penetration testing works (Moustafa, 2021). In addition, the use of Wireshark in real life cases will show its ability to increase security. Vulnerabilities in configurations, protocols, or user authentication mechanisms can be uncovered, by analysing captured packets. This insight is valuable for designing targeted mitigation strategies (reducing gaps in firewall rules, encrypting in transit communication). Wireshark allows to verify these measures by comparing network traffic before and after made security changes. Becoming a part of the security framework and adding Wireshark to it gives organisations , GigaTec IT, the tools to be able to discover, assess, and rectify any potential threats. Additionally, it has a role not limited to threat detection, but also a diagnostic use as a tool to validate the robustness of network defences. This research emphasises the importance of sustained chutzpah and technical acumen in deploying such methods as Wireshark in secure modern networked environments.
The first key step to effectively deal with network vulnerabilities is to setup the environment to analyse and secure the Networks. The first step to setup of the rig is installing of Wireshark as the main tool for networking analysis, and other support utilities to facilitate testing. Capturing and analysing network traffic is an invaluable feature of Wireshark which enables the tool to identify potential threats and cheque how the data is flowing (Guo et al., 2024). Two user accounts are created here in the system, one with the Superuser access to perform administrative duties and another user with the standard user access for performing the day to day tasks. By setting up like this, this allows for a realistic simulation of user roles and permissions in the network environment, which is quite similar to the kind of organisation most GigaTec uses, starting with its IT division (Mahor et al., 2021). The rig is hardened against common security vulnerabilities by implementation of baseline security. The rules are established in firewall that manages traffic flow between the PCs and allows only the authorised communication, also the permissions of the users are set so that they could access the facility only. They provide a base layer of defence to this system by rendering it safe during testing. GigaTec-IT’s network environment is simulated by the rig, which is set up to simulate the operation of a normal environment: web traffic, files sharing, and user interaction. This is a controlled, but realistic means for conducting security tests and finding weak points (Oikonomou et al., 2022). A detailed testing plan is designed to be followed to use Wireshark to analyse a network security. Traffic scenarios such as TCP communications, IGMPv3 multicast messaging, ARP requests, and encrypted TLSv1.2 exchanges are captured by the plan. These are common network activities which are good scenarios for assessing the rig’s measures for its security. Wireshark’s filtering abilities make it possible to isolate particular packet types for further inspection, to identify irregularities, or at least potential threats.
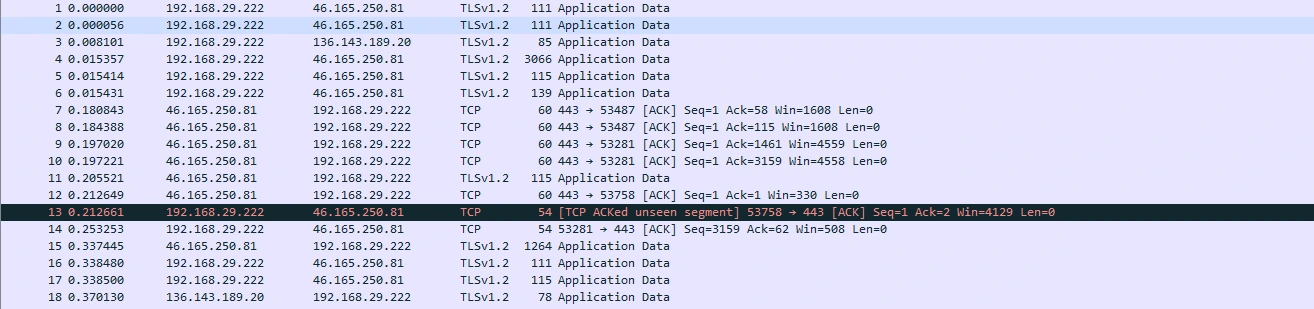
Figure 1: All data of IP address
The testing is expected to detect anomaly in the traffic patterns, identify misconfigurations and confirm the existence of secure communications (Kilincer et al., 2021). The number of unauthorised access attempts, traffic volume on certain ports, and the level of encryption of critical data serve as metrics indicating system security position. The results presented here serve as a basis to evaluate the effectiveness of the implemented measures and also pinpoint areas to be further improved. Following this structured approach, the pre-engagement phase creates a good base for a detailed and credible security analysis of a network.
Get assistance from our PROFESSIONAL ASSIGNMENT WRITERS to receive 100% assured AI-free and high-quality documents on time, ensuring an A+ grade in all subjects.
Some of the potential vulnerabilities identified were captured through network traffic with the configured environment using Wireshark. The tool was brought up on the Ethernet adapter associated with the network interface that is active and therefore all traffic from and to the system was monitored (Abosata et al., 2021). Network activities were performed including accessing websites, starting TCP connexions, and simulating multicast requests (IGMPv3) with live packet capture enabling. All captured packets were analysed in real time and their filtering capabilities in Wireshark were used to isolate specific protocols such as TCP and TLSv1.2.
Figure 2: data of TCP
Examples include observing open ports on TCP traffic observable to external traffic that could be exploited, and IGMPv3 traffic indicating misconfigurations for multicast networking, and TLSv1.2 to confirm the integrity of encryption (Mateus-Coelho et al., 2021). The suspicious packets included from unknown IPs were being flagged for further inspection. To cite just one example, suspicious ARP requests that contained no valid replies might have indicated attempts to gain unauthorised network information by mischievous means. They used these findings as a basis for mitigation strategies and closed vulnerabilities in such a systematic way that they could not be exploited.
Figure 3: Ethernet adapter VMware Network Adapter
To resolve the vulnerability which implemented multiple ways and validated it using wireshark. Analysis revealed open ports which are then secured by the update of firewall rules to restrict access. Those access control lists blocked traffic from untrusted IP addresses. Hence, to respond to an instances in which weak authentication was detected, system configurations were changed for implementing stronger password policies and two factor authentication.
Figure 4: data of IGMPv3
These changes were validated by Wireshark. Packet captures post mitigation showed a reduction in unauthorised traffic and previously accessible ports became blocked. Secure handshakes without downgraded protocols were re-evaluated of session TLSv1.2 encrypted sessions (Garg and Baliyan, 2021). The system was also optimised to respond to multicast traffic, and filtered IGMPv3 requests only reported authorised sources communicating in the network. The improvements dramatically improved the system’s security posture, reducing the system’s attack surface while preserving functionality.
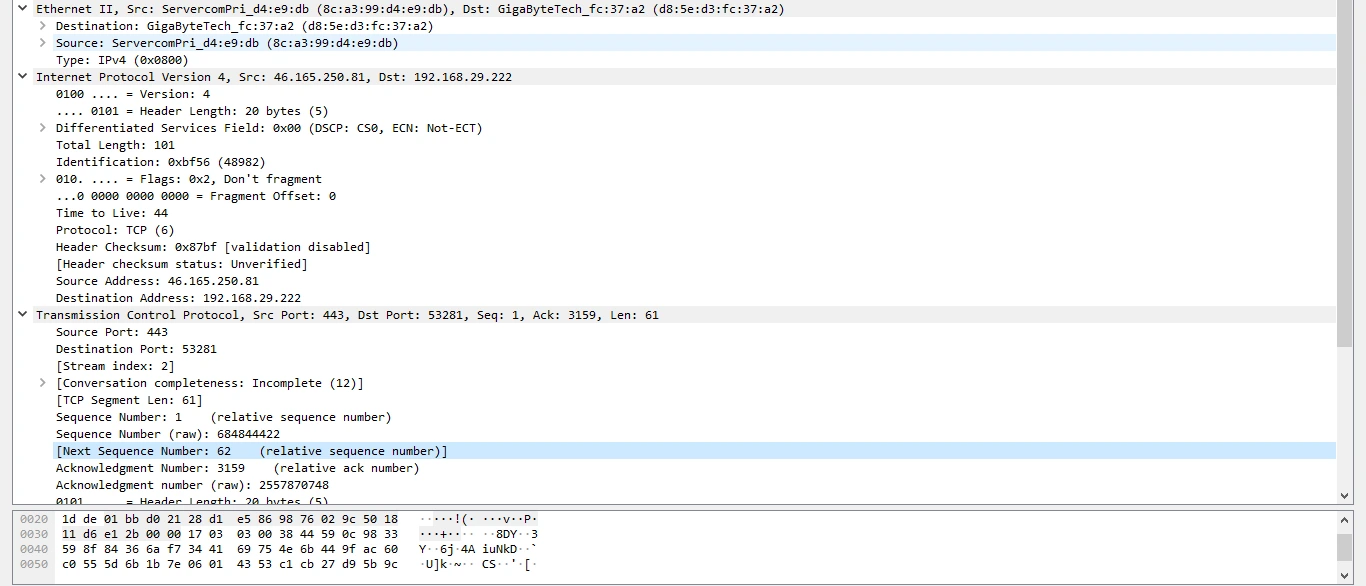
Figure 5: data of Ethernet II
Scripting for Automation
Automation scripting was crucial in moving security processes to be more streamlined, requiring less manual effort, and more accurate. I thought it was a good idea to come up with a Bash script to run scheduled scans for open ports, log the results, and alert admins when something changed (Narwal and Mohapatra, 2021). They took a proactive approach that would ensure that he would be able to catch any unauthorised change on the network configuration and respond before it escalated into a crisis. User account management was also automated via scripting. With the automation, newly created accounts were on strict security protocols — with password complexity requirements and configured permissions. This removed inconsistencies which normally occur when creating accounts manually. In order to further increase efficiency, log parsing scripts for analysing anomalies and potential threat in Wireshark captured data were developed. The scripts ran on large amounts of data and spotted patterns as signs of malicious behaviour or network vulnerabilities. This automated the task and reduced the time and effort required to interpret network traffic data so that could respond quickly when something was amiss. These scripts were validated as effective using Wireshark. Scanning and configure were monitored through automated scans and configurations to see that they happened as expected. The packet captures (using Wireshark) confirmed that the scripted processes—port scans, anomaly detection, and so on—were consistent with what one would expect from a system that’s adhering to security standards. This automation of these tasks prevented human errors, while also triggering a more proactive and scalable model in threat detection and response that improved the security posture of the organization.
Findings were consolidated in the post-engagement phase with a focus on assessing mitigation effectiveness and providing actionable recommendations for long term security improvements. Analysis of the platform identified several key vulnerabilities as it analysed open ports exposed to unauthorised access, weakness in authentication protocols, and unfiltered multicast traffic. Such issues presented a significant risk – unauthorised access, data interception, denial of service attacks etc. These concerns were addressed by the implemented mitigation strategies. Updated firewall rules restricted traffic to vulnerable ports; access control lists blocked untrusted IP addresses; and stronger authentication is enforced, including two factor. Reduced unauthorised traffic, closed access to sensitive ports and use of secure encryption are verified from post-mitigation Wireshark captures (Mughal, 2022). However, despite these successes additional enhancements are needed to sustain a robust security posture. A real time monitoring and alert for suspicious activity may be obtained from introducing an intrusion detection system (IDS). It suggests that regular security assessments are done to discover the emerging risks. Besides, centralised logging systems and high end analytics tools for detection and response to threats can be implemented. Additional defence would succeed in the organisation by adopting best practises such as periodic training for IT staff, enlisting in stricter endpoint security measures. The project itself raised several challenges, including extracting tidy datasets from large quantities of captured network traffic, as well as recognising legitimate versus suspicious activity. Nevertheless, the obstacles of these steps have provided useful lessons regarding what can be done with Wireshark in practical use. For traffic analysis, the tool proved a gold mine, enabling us to go deep into packet level data and identifying vulnerabilities. At the same time, it was shown useful in validating the efficacy of mitigation strategies like secure configurations and better authentication mechanisms. The engagement in general indicated that proactive protection, multiple layers of protection are needed in cybersecurity. This experience showed the role Wireshark can be in the realm of both investigation and validation, closing the gap between theory and real world application. In this project, continuous monitoring was put forward and thought to be essential for ongoing threat observations, updates, and adaptations to combat current and future threats both systematically and enable.
Conclusion
Operating Systems and Networks have to be secured to protect organisational data, enabling them from being accessed by unauthorised entities, disruptive services, and data breaches. The fast moving landscape of today’s threat landscape demands proactive steps to minimise risk and preserve operational integrity. An end to end robust security framework is an absolute guarantee to safeguard sensitive information, maintain business continuity and ensure regulatory compliance. This project has benefited greatly from Wireshark, which has helped it identify and analyse network vulnerability. The examination of such problems as open ports, weak authentication protocols and unfiltered traffic are the kind of thing with which it could expose the aching on the inside of the machine through detailed packet inspection. It was able to dissect encrypted sessions, and analyse the handshake process to ensure secure configurations were deployed correctly. Additionally, real-time network traffic was validated on Wireshark to establish the case for mitigation strategies, as it showed the closure of vulnerabilities as well as the integrity of the security measures applied. Continuing monitoring and adaptive security measures were emphasised through the project. Powerful capabilities of Wireshark filled the gap between theory and practise and allowed practitioners to gain a practical view of securing complex systems from front to back. While threats may change, using Wireshark along with regular audits and proactive defences give organisations the ability to use tools such as Wireshark and be able to continue to have resilient operating systems and networks that can protect themselves against risks and remain robust and secure.
Reference List
Journal
Introduction to Occupational Risks Prevention Assignment The purpose of this work is to propose the creation of a new...View and Download
Introduction Get free samples written by our Top-Notch subject experts for taking online Assignment...View and Download
Introduction -Reflective Commentary Portfolio Reflective Commentary refers to semi-formal report that accompanies piece of...View and Download
Chapter 1: Introduction For students diving into the complex world of psychiatric genetics, College Assignment Help offers...View and Download
Introduction: Driving Climate Action with AP4CA Connect with our expert Assignment Helper, for Professional support in...View and Download
Introduction Get expert support with an assignment helper focusing on tourism, social bodies, and sensory engagement to enhance...View and Download
