+44 75754 30035 help@rapidassignmenthelp.co.uk
offer
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
The purpose of this assignment help research is to describe the existing cybersecurity issues and measures in the context of teleworking. This paper seeks to understand how the cybersecurity environment has changed as organizations around the world adopt decentralized work environments. The main purpose of this report is therefore to explore the complexity of the issues of managing cybersecurity in remote environments in terms of technological, organizational, and individual aspects. The study also covers areas of interest like security of cloud-based collaboration tools, Zero Trust Architecture, Bring Your Own Device (BYOD) policies, network security for remote connectivity, incident response in distributed environments, regulatory requirements, and the use of advanced technologies like artificial intelligence in threat detection.
This section explores the key cybersecurity challenges faced by organizations adapting to remote work environments. It highlights increased risks such as unsecured home networks, vulnerabilities introduced by personal BYOD devices, and the expanded attack surface for cybercriminals. The importance of implementing robust solutions like Zero Trust Architecture, multi-factor authentication, and continuous employee training is emphasized to mitigate threats. Additionally, the use of artificial intelligence for advanced threat detection and automated incident response is discussed. This section underscores that effective management of cybersecurity in remote work settings requires a combination of technological, organizational, and regulatory strategies to safeguard corporate resources and data.
Relevance:
Borkovich et al. 2020, focuses at the dynamics in cybersecurity in the context of remote working. The authors describe the areas of risk associated with the use of personal devices, home networks, and less physical security measures. They assess the expanded attack surface and then explain why and how the traditional security must be rethought. The paper will be of significant value for organizations operating in remote geographical areas and dealing with cybersecurity threats; the paper highlights current trends in those threats. It underlines the need to come up with effective solutions of handling these issues, an area that is in line with the main study area of managing cyber threats in the context of remote working.
Relevance:
In the views of Khan, 2023, the use of Zero Trust Architecture as an architecture for remote work as a security model. The authors elaborate that through applying this approach, which does not presume that access can be trusted, the risks of the distributed workforce access to the company’s resources are addressed. They examine concepts like, always on authentication, the principles of least privilege access as well as micro-segmentation. As such, the study provides useful suggestions for improving security in contexts of remote working, which is a direct response to the problem of protection against cyber threats in distributed settings. It offers a helpful information to the organizations that aspire to better prepared in the security of the newly emerged remote work environment.
Get assistance from our PROFESSIONAL ASSIGNMENT WRITERS to receive 100% assured AI-free and high-quality documents on time, ensuring an A+ grade in all subjects.
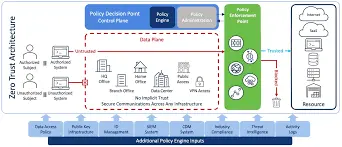
Figure 1: How to implement Zero Trust Architechture
Relevance:
Hijji and Alam, 2022, explores the significance of the employee training to enhance cybersecurity measures of the employees working from home. The authors also stress the need to carry out training and security awareness programs from time to time in order to ensure that the remote workforce is security conscious. They focus on the best strategies to use in the training process such as dummy or mock phishing and other forms of training exercises. The research gives understanding into effective broad training interventions that can address specific issues of remote work. The paper provides managerial implications for organisations that want to engage employees as the primary line of protection against cybersecurity threats, which contributes to addressing the management of cybersecurity risks in the context of remote working.
Figure 2: The role of employee training and awareness
Relevance:
Borissova et al. 2020, focuses on the risks that are encountered in cloud-supported collaboration tools in the context of teleworking. The authors discuss threats including unauthorized access, data leakage and insecure file sharing. Such considerations outlined include the adoption of end to end encryption, strong access controls and security audits amongst others. The paper also presents case studies of real-world attacks on popular collaboration tools and service, as well as lessons learned. This also includes practical guidelines on how to configure and secure the usage of these tools and how to educate users as well as enforce policies in relation to their usage. The paper also looks into the improvement of these tools in tandem with other security information and event management (SIEM) systems for identifying and combating risks applicable in remote work environments.

Figure 3: SIEM
Relevance:
Njuguna and Kanyi, 2023 analyses the security issues related to the use of own devices in working from home environments. The authors consider some of the threats that include loss of the devices, presence of malware, and unauthorized access of personal data. They talk about issues related to the secure management of the device, where they cover MDM, containerization and the ability to wipe devices remotely. The paper also discusses the policy solutions that seek to address privacy and protection of employees as well as organizational security. This is a discussion of several organizations that have adopted BYOD policy and the lessons that can be learnt from them. Thus, the paper also explores the part of the employee education in avoiding the BYOD risks and outlines the risk assessment framework for the organizations that are planning to implement or improve their BYOD strategies in the context of the remote work.
Relevance:
Vinoth et al. 2022, focuses on protection of the network link mainly concentrating on remote access to business networks. The authors explore the different types of VPNs explaining the effectiveness and the weakness of using them in the context of remote work. They talk about encryption algorithms including AES-256 and how the help in securing data in motion. The paper examines the possible new ideas such as Software-Defined Perimeter (SDP) and how these can help in improving the security of remote access. This responds to the need for an assessment of the effectiveness of different multi-factor authentication techniques such as biometrics and the use of hardware tokens in a working from home environment. It also looks at the issues of security in remotely accessible legacy systems and ways of implementing incremental improvements in security while avoiding service disruption.
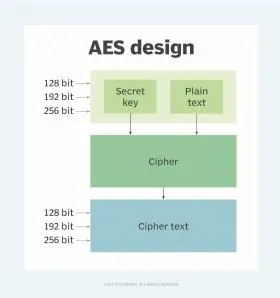
Figure 4: Advanced encryption standard
Relevance:
Tatineni and Mustyala, 2022 detailed discussed on cybersecurity incident response and management, a consideration of remote work. The authors focus on the issues related to the integration of the response activities in the geographical space. Some changes to the well-known incident response models are given, stressing the importance of communication and roles in the distributed environment. This paper provides an overview of a model for remote forensic examination, and considerations of legal and technical implications. This also describes how the use of automated response systems as well as Artificial Intelligence based analytics can be used to enhance the ability to identify and respond to incidents. The study presents several examples of effective management of incidents in the context of remote working, highlighting key insights and recommendations for organizations that are adjusting their approaches to managing incidents.
Figure 5: A complete guide on AI based data analytics
Relevance:
Rakha, 2023 explores compliance and regulatory issues on remote work cybersecurity. The authors discuss the effects of data protection laws including GDPR and CCPA on remote work procedures. They also talk about how the compliance can be maintained in distributed environment and some of the techniques covered are data classification techniques, access control techniques, reporting and audit trail techniques. The paper also discusses the issues faced in doing remote security audits and comes up with methods for virtual assessments. It analyzes standards specific to particular industries (i. e., HIPAA in healthcare, PCI DSS in the financial sector) and their effects on the security of remote work. The study also fits into the dilemma of cross-border transfer of data in the global remote teams and offers directions on how to approach the international data protection frameworks.
Relevance:
Zaman et al. 2021, discusses on the use of AI and ml in cybersecurity in the context of the new normal of remote working. The authors identify how threat detection can be improved through the use of tools which are powered by artificial intelligence; this includes looking at traffic patterns within a network and the activity of users in order to determine what is unusual. They talk about how machine learning can be used in predicting and mitigating the chances of getting phished, which is rife in remote settings. The research focuses on the possibility of using AI to automate the security processes such as patching and vulnerability scans on the distributed systems. It also discusses the issues which are closer to the application of AI-based security solutions, including the issues of data preparation and adversarial attacks.
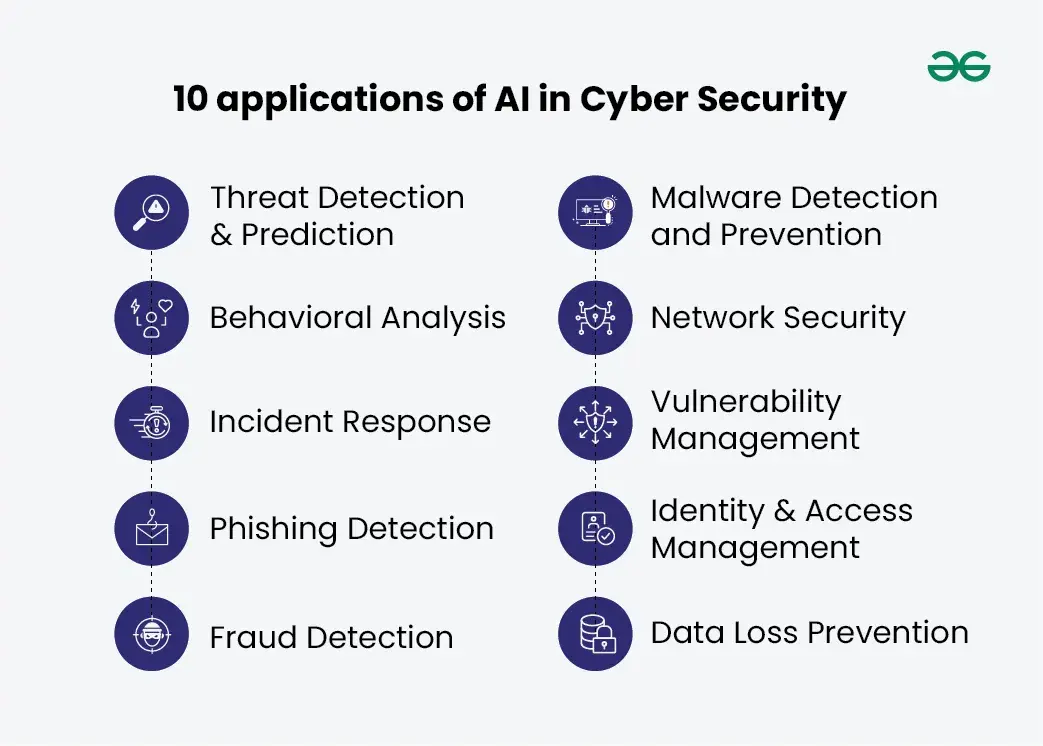
Figure 6: Application of Ai in cyber security
Relevance:
In the views of Palumbo et al. 2021, The issue of security versus usability in remote work environment is one of the prominent topic that need to be focuses on in these days. The authors look at the effect of security measures on employees’ productivity and their job satisfaction levels. They talk about how to make security controls effective and at the same time, user friendly including the issue of single sign-on options and context based access policies. This paper offers a model for evaluating system security tools and methodologies in distant contexts. It discusses how user experience design is used in the construction of security measures that make the user conform to the set rules, not find ways around it.
Conclusion
The analysis of the cybersecurity threats and opportunities in the remote work context present a picture of a rapidly developing space that requires an integrated approach. The conclusions confirm that existing strategies should be more flexible covering both technical and human sides of the problem. Some main topics highlighted are the need for effective security in cloud, the idea of how Zero Trust architecture can address challenges posed by the distributed work-force, and the idea of flexibility of security and usability. The study also discuses the increasing importance of artificial intelligence and machine learning in fortifying threat identification and management. Moreover, the study ascribes significance to the training of the employees, the policies guiding the use of the devices, and the flexible handling of security incidences particularly where remote working is concerned. Since the COVID-19 outbreak, work from home and hybrid work setups have become the norm and companies must stay alert always on changing risks and constantly modifying security policies to meet new and changing regulations.
Reference list
Journals
Introduction: The Contemporary Hospitality Industry Hospitality industry is the most dynamic and competitive service industry...View and Download
Introduction - Strategic Business Analysis of T4 Tea Company Get free samples written by our Top-Notch subject experts for...View and Download
Introduction Get free samples written by our Top-Notch subject experts for taking online Assignment Help services. A...View and Download
Introduction The world of work is referring to dynamic environment determined by different aspirations, skills and motivations...View and Download
Finance For Strategic Managers Assignment Sample Introduction: Finance For Strategic Managers Assignment Sample Get free...View and Download
Introduction Get free samples written by our top-notch subject experts by taking the Assignment Helper service from Rapid...View and Download
