+44 75754 30035 help@rapidassignmenthelp.co.uk
offer
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
Need cybersecurity assignments like this? Assignment Help UK delivers expert academic writing, helping you master Cisco networking and security concepts easily.
This report describes key cybersecurity ideas and technologies for defensive your network using Cisco systems. It examine the NIST cybersecurity framework for hazard-based safety, after which provide an explanation for how the Wireshark community protocol analyzer can be exploited via attackers. Next, It can show how the WannaCry ransomware and TeleRAT Trojan are allotted. Additionally, we discuss strategies to guard in opposition to phishing attacks together with whaling and pharming. Additionally, this paper describes a redundant community topology advanced with Packet Tracer for excessive availability purposes. Finally, it introduce Cisco safety solutions for get entry to control, encryption, and threat detection.
The NIST Cybersecurity Framework performs a essential position in defensive virtual assets and personal statistics in state-of-the-art related society by using presenting corporations with a hazard-based totally method to coping with cybersecurity. As it defined in the creation, cybercriminals follow a careful plan and undergo numerous degrees referred to as the kill chain & quot ; before launching an assault. The NIST framework acknowledges this evolving chance panorama and offers companies with steering on threat assessment, asset safety, malicious hobby detection, incident reaction, and attack recuperation. The NIST Cybersecurity Framework describes a bendy, chance-based technique that permits agencies to personalize their cybersecurity packages primarily based on their individual danger profiles and tolerances. This is vital due to the fact it recognize that every company's information structures, vulnerabilities, and danger appetite can vary substantially. A blanket mandate or recipe is neither realistic nor powerful. More specially, this framework allows companies systematically examine cyber risks in their structures, belongings, facts, and skills. This consists of identifying threats, reading vulnerabilities, determining capability effect and possibility, and using this analysis to prioritize moves. Organizations can adapt by way of categorizing their systems and records, choosing core security controls, and determining responses to mitigate high-precedence dangers[7]. For example, corporations with massive amounts of sensitive consumer records may also prioritize more potent get right of entry to controls, encryption, and pastime tracking. On the alternative hand, people with older legacy structures may attention on system enhancements and backups. Essentially, a risk-based totally technique presents context-primarily based autonomy while providing quality exercise requirements to manual improvements[8]. This permits clever agencies to get the maximum value from their cybersecurity investments in step with their own tolerances, constraints, and goals. Specifically, this framework consists of 5 concurrent features: identify, guard, come across, reply, and recover. The Identification feature is centered on increasing an enterprise's understanding of a way to manipulate cybersecurity dangers. This includes asset control, chance assessment, and impact evaluation[6]Protection describes safety features that help ensure the provision of critical offerings which Identity and Access Management, Data Security, Protection Technologies and Policies. Detection capabilities provide a way to discover cybersecurity events in a well timed way through a continuous tracking and detection system. Response abilities include appropriate activities to take action on detected cybersecurity incidents. Finally, recovery competencies identify the suitable sports had to hold resilience and restore functionality suffering from the incident. The NIST framework's five concurrent talents provide a high-level strategic view of coping with cybersecurity risks to an organization's human beings, processes, and generation. These functions recognize that mere precautions are not enough[7]. Organizations also need danger focus, non-stop monitoring, mitigation plans, and the capability to renew operations. The framework facilitates a proactive in preference to reactive approach by means of enabling businesses to view all 5 domain names collectively in preference to in silos, and powerful cyber threat management requires emphasizes the need for continuous and simultaneous adjustment of the features of the Introducing controls in simplest one or areas creates incomplete protection and exposes gaps. In summary, the NIST framework recognizes that no employer can prevent all assaults. However, through offering a flexible threat-based approach that may be tailor-made to an enterprise's wishes, organizations can determine their chance tolerance, enforce suitable security measures to guard essential property, and protect in opposition to malicious attacks. Detect interest, reply to incidents, and get over assaults. Therefore, it performs an vital function in protective touchy information and retaining privacy in state-of-the-art virtual age[9].
This comprehensive understanding of cybersecurity frameworks is essential knowledge for students completing programming assignments related to network security.
Wireshark is an open-supply community protocol analyzer that cybercriminals can use to acquire touchy data approximately a target's community for the duration of the reconnaissance section of an assault. Specifically, Wireshark allows an attacker to capture and investigate all traffic passing thru a network phase. By putting the network interface of a tool walking Wireshark into promiscuous mode, the tool can covertly intercept and record all community packets, even those not intended for that tool. Wireshark allows comprehensive network reconnaissance through an attacker in 4 important methods: First, Wireshark allows mapping of the goal's network topology with the aid of intercepting site visitors among gadgets and revealing her IPs, hostnames, domain names, subnets, routers, and related systems. This absolutely exposes the format of your infrastructure.
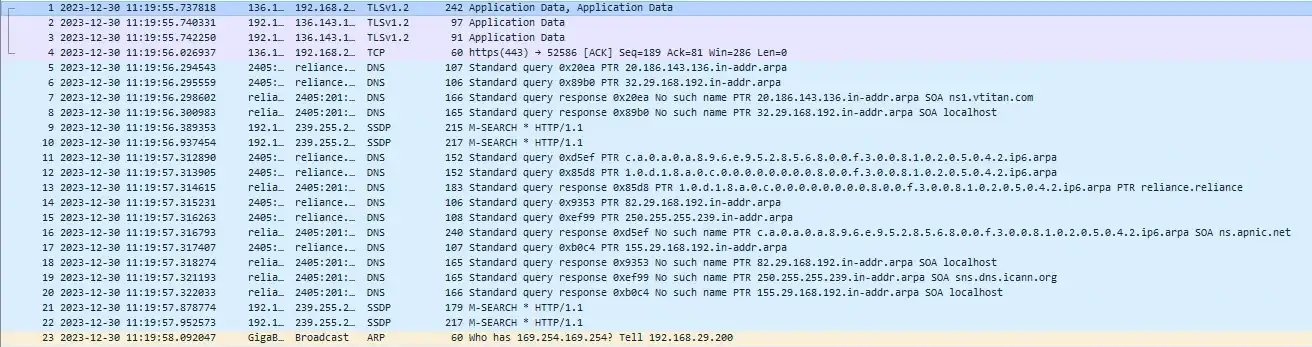
Figure 1: Data table of the various protocol
Then, by way of searching at open ports and communication, Wireshark determines what working device, provider version, mail server, database, and so on. Attackers find goals to make the most[5]. Third, unencrypted HTTP, FTP, Telnet, and other protocols can permit direct eavesdropping on usernames, passwords, files, and touchy periods. This permits brazenly transmitted information to be stolen. Finally, tracking common styles in the amount of visitors among network segments can tell attackers about such things as height utilization instances and big transfers. These planning insights support green assaults. In brief, Wireshark provides dangerous insights into your goal's humans, tactics, technology, their patterns, systems, and statistics flows. This makes it less difficult for attackers to perceive vulnerabilities[10]. Although Wireshark has valid makes use of, it's far important to put in force strong encryption and pastime tracking to limit the interception of unauthorized traffic. Allowing such network mapping is an essential first step in addressing the risk of cyberattacks.

Figure 2: output
Nmap is an open-source network scanner that can be misused by attackers to map out and reconnoiter a target's network. It can uncover network topology, identify operating systems and services running on hosts, intercept unencrypted credentials and traffic, analyze usage patterns, and generally expose the infrastructure for malicious reconnaissance. While Nmap has legitimate purposes, attackers can leverage it during initial reconnaissance to gain insights that enable exploitation of vulnerabilities[11]. Implementing encryption, access controls, and activity monitoring helps mitigate these risks from network mapping. Ultimately Nmap illustrates the importance of limiting unauthorized visibility into networks to proactively improve security posture against threats.
Get assistance from our PROFESSIONAL ASSIGNMENT WRITERS to receive 100% assured AI-free and high-quality documents on time, ensuring an A+ grade in all subjects.
Figure 3: Nmap output
Whaling is targeted phishing that especially objectives senior executives and bosses inside an organization. The attacker sends the victim a fake e mail that looks to return from a trusted supply that the govt may recognise, inclusive of a provider, legal professional, or supervisor. This e-mail is meant to seem severe and pressing, and often contains essential requests or links to sensitive information to get the victim to click. However, the hyperlinks and attachments are sincerely malware designed to steal login credentials or, if clicked, deploy malware that allows data theft. Because executives often have privileged get entry to to touchy systems and records, successful whaling attacks can exploit the expanded privileges of compromised government bills to cause large harm, economic fraud, and Intellectual belongings theft might also arise. Therefore, groups want effective user training, e-mail security, endpoint protection, and perimeter controls to shield against government whaling operations.
Pharming is a phishing approach which attack on the Domain Name System (DNS). It redirects customers to a faux her website managed by way of the attacker. Farmer is capable of hijack site visitors destined for her valid website by way of abusing DNS servers and converting DNS information and gadget settings on customers' gadgets. These redirect traffic to faux and deceptive copies designed to imitate the look and URL of the genuine internet site. When journeying a fake pharming website, sufferers log in or input economic statistics without knowing they may be on a authentic web page. Attackers then steal this touchy facts for identity robbery, price fraud, or account takeover. Pharming bypasses different defenses, together with email filters, by way of manipulating the connection from a browser to a website rather than forcing the victim to click on a hyperlink[12]. Therefore, technical protection measures along with DNS protection, proxy filtering, SSL inspection, and endpoint monitoring are required to dam connections to faux web sites and save you stolen facts from being sent to attackers.
Benefit from the expertise of our skilled tutors. Our Assignment Help England team delivers original, in-depth cybersecurity and networking assignments tailored to your needs.
Effective protection requires a layered technique to protection across humans, methods, and era. Users are the maximum centered connectors. Security awareness training will soon be implemented to assist employees pick out fraudulent emails and web sites. Technical controls provide extra protection. DNS filters seize redirects to faux websites, proxy firewalls block botnets and command servers, and often updated blacklists flag newly registered phishing web sites. Endpoints are protected with patched structures, anti-malware to dam infections, and information loss safety. Email Security gets rid of suspicious attachments and hyperlinks through powerful filtering and sandboxing. Multi-element authentication provides an extra layer of verification of a consumer's identification. Using MFA, up to date software program/filters, consumer training, DNS protection, proxy firewalls, and electronic mail safety together will make it a great deal extra tough for phishers and farmers to penetrate defenses and save statistics loss.
(ii) Whaling targets senior executives and executives inside an employer with spear phishing emails that seem proper and urgent. These faux emails impersonate real vendors, clients, lawyers, or managers that the goal may additionally realize. The goal is to trick victims into clicking on malicious hyperlinks or establishing infected attachments as a way to assert their authority. Once clicked, a whaling assault can scouse borrow login credentials, deploy malware, or access sensitive organisation records and debts. Because executives regularly have get right of entry to to privileged accounts, those breaches may be extremely negative. Pharming is a phishing approach that hijacks the Domain Name System (DNS). Traffic that redirects website site visitors to a fake malicious replica of her website controlled via the attacker[4]. By manipulating DNS statistics, server settings, or host documents on sufferers' computers, Farmer ought to direct customers who appeared to be journeying her valid website to a fraudulent reproduction as a substitute. These fake web sites are designed to mimic and duplicate the look of the actual her internet site.;Users may additionally unknowingly offer their login credentials, private records, credit score card numbers, or other sensitive facts at once to the criminals running the web site, leading to identity theft the usage of compromised bills. Financial fraud becomes viable[13]. To guard yourself from pharming, you need to secure your DNS infrastructure and train your employees to become aware of fraudulent websites. Pharming involves hijacking the Domain Name System (DNS) [2]. Traffic that redirects internet site site visitors to a reproduction of her page loaded with malicious malware managed by the attacker. By manipulating DNS data, server settings, or host documents, Farmer directs unsuspecting customers to her faux female friend website in place of her actual one. Users then input passwords, non-public information, credit score cards, and so forth. Amassed through the criminals. Effective pharming safety consists of DNS filters to intercept redirect tries, proxy filters to dam botnet command pages, URL reputation to identify newly activated phishing pages, endpoint protection to stop malware, and prevent disclosure. Multiple layers are required, consisting of employee education for Avoid information at the net. User education makes a speciality of phishing detection, and technological protections inclusive of subsequent-generation firewalls, net filters, DNS protection, patches, and location authentication measures inclusive of Extended Validation (EV) SSL help locate assaults early and prevent damage. Is meant to minimize. The modern day danger intelligence allows you to react to new pharming and phishing techniques before a chief incident occurs[3]. A aggregate of layered generation defenses and normal cease-consumer education can assist reduce pharming dangers and different phishing attacks aimed toward stealing credentials and touchy information for fraudulent purposes.
The network utilizes redundant firewalls in active-standby configuration, removing the firewall as a single point of failure. Distribution layer switches are connected via crossover links using spanning tree to enable failover between VLAN routing. EtherChannels bundle links between access switches and distribution for bandwidth and redundancy. If an individual switch, port or link fails, traffic can be dynamically redirected through the redundant paths. The redundant components combined with the automatic failover enabled through spanning tree and EtherChannel delivers high availability by eliminating single points of failure that could disrupt connectivity.

Figure;4: Cisco Model
(ii) The distribution layer switches are directly interconnected through crossover links. Spanning tree protocol is enabled on these links to prevent switching loops while providing redundancy. If one distribution switch fails, spanning tree will automatically disable the crossovers to that switch and enable the redundant path to the other distribution switch. This allows routing between VLANs to remain operational using the second distribution switch. The spanning tree enabled crossover links between the distribution switches eliminate a single point of failure and enable automatic, reliable failover if one switch goes down. This delivers high availability through built-in redundancy and failover at the distribution layer.
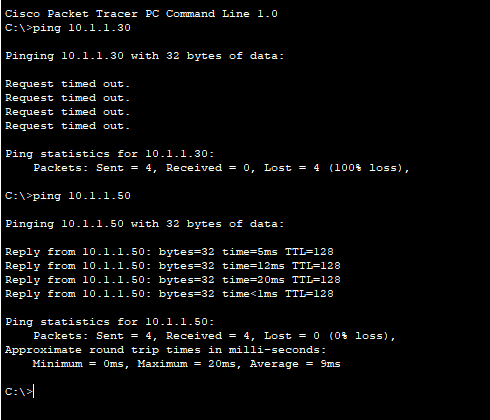
Figure 5: Deny ping and permit ping
;Cisco offers superior software program and hardware protection technology that you could enforce to defend your operations across diverse community areas. For perimeter security, subsequent-era Cisco firewalls along with Firepower NGFW offer included Provides risk safety[1]. This protects you from recognized zero-day threats that try to infiltrate your community. To stable internal LAN get entry to and traffic, Cisco Identity Services Engine (ISE) can provide satisfactory-grained policy-based totally get entry to manipulate[14]. Cisco Stealth watch’s encrypted visitors analysis also permits behavioral monitoring to fast discover threats that pass traditional gear. Additionally, technology along with MAC sec encryption and Cisco Trust Sec facts plane cryptography solutions can be applied at the transfer to encrypt connections and site visitors flows between key community segments and safety zones. Segmentation contained threats[15]. It combines advanced tracking, get admission to manage, encryption, and AI-powered risk analysis on community devices to deliver cease-to-end proactive built-in safety to protect vital business structures even as mitigating protection breaches.
This report covers basic cybersecurity topics such as NIST requirements, malware threats, phishing risks, network redundancy principles, and Cisco security solutions, but those areas are open to in addition studies. Future paintings consists of accomplishing realistic experiments using equipment such as Wireshark for ethical hacking scenarios that complement the concepts mentioned. It additionally adds fee to test the reliability of the proposed excessive-availability network layout thru packet tracer simulations of various failure situations. Additionally, information on configuring and tuning Cisco firewalls, ISE, Stealthwatch, and subsequent-technology encryption solutions can be supplied to demonstrate actual-international implementations. You also can hold your content updated with further analysis of recent attack techniques and appropriate shielding strategies.
Recommendation
This document offers a stable foundation and covers important cybersecurity ideas, threats, defenses, and Cisco answers. Gain foundational expertise by way of studying the NIST framework, malware assaults, phishing techniques, network redundancy concepts, and Cisco security technologies. However, a few extension recommendations may be helpful to the reader. First, the guide might be extra realistic through which include extra realistic demonstrations, laboratory configurations, or packet tracer simulation results related to the topics being discussed. Additionally, investigating new assault techniques including social engineering, evasion tactics, and cloud vulnerabilities can also find new threats. Keeping content up-to-date with evolving risks and related mitigations maximizes destiny relevance for cybersecurity groups, community specialists, and era leaders seeking to guard critical infrastructure.
Conclusion
This file offers key insurance of networks and cyber security essentials using cisco essential cybersecurity standards that leverage Cisco technology to guard your community. It examines the function of standards consisting of the NIST Risk-Based Security Framework and offers an overview of malware attack vectors including WannaCry and phishing methods together with whaling and pharming. Network redundancy ideas with an emphasis on high availability are also defined and modeled in Packet Tracer. Additionally, key Cisco hazard safety solutions together with next-era firewalls, ISE, encryption, and Stealth watch are highlighted. While further fingers-on demonstrations of these technology would be beneficial, this report establishes the foundational cybersecurity, networking, and Cisco knowledge that era experts can construct upon to protect critical systems and information.;
Reference List
Journal
INTRODUCTION: Sainsbury's Global Marketing Struggling with global marketing management assignments? Assignment Help UK delivers...View and Download
Introduction to the Principle of International Business Assignment Primark is a global fashion retailer providing employment to...View and Download
Introduction: Level 5 Business Ethics Business ethics refers to the moral principles & values which direct how organisations...View and Download
Introduction Get free samples written by our Top-Notch subject experts for taking online assignment services. This report...View and Download
Introduction: Life Course Approaches to Health and Ageing Middle life is commonly referred to as the period between the ages of...View and Download
1.0 Introduction Score top grades with Rapid Assignment Help’s student-focused and high-quality Assignment Help...View and Download
