+44 75754 30035 help@rapidassignmenthelp.co.uk
offer
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
🎁Special Offer 🎁 Discounts - Up to 55% OFF!
Future Project (FP) is a mid-size company that deals with customers’ sensitive information. For students seeking help writing assignments on network security implementation, this FP case study demonstrates practical solutions. When handling such an organization, there is a need to ensure that the network has been fortified and protected against any form of cyber attack. Lately, FP suffered a small-scale data leak implying that there are weaknesses in the organization’s network that needs to be addressed. This resulted in unauthorized access into the customers’ information and potential threat to the operations of FP.
Thus, FP must upgrade its network security standards to avoid further risks of cyber threats in the future. Two important areas within networks that are critical to managing the protection of data as well as controlling access and enhance performance is Network Security. The functionalities such as router security measures, the firewalls (ACLs), VLANs, and security policies will improve the general network integrity and confidentiality.
This paper covers the description of the network security needed in FP as follows:
How to prevent single points of failure in a network while aiming at attaining a good design for network topology that is both secure and scalable.
One needs to admit that ensuring router security has its measures like passwords and encryption.
Implementing IP Access List for permission or banning of certain IP address.
As a segmentation method in a network, VLANs are effective in the reduction of security threats.
A comparison of the OSI and the TCP/IP models in the use of securing the network communication.
The above listed best practices in network security will ensure FP acquires effective and efficient network protection for their operations and customers information from acts of cybercrime.
Network topology refers to the arrangement and organization of a network that is used for describing the flow of data and connectivity of the various devices in the system (Lei, 2023). In choosing the type of topology for the new LAN configuration that FP is to establish, Star Topology has been adopted since it is scalable, reliable, secure, and easy to diagnose when a certain segment is faulty.
Justification for Star Topology
Scalability
New devices can be added to this system without a conflict of interest with other devices connected to the same system.
Also, it guarantees future growth as FP expands its business to other areas.
Reliability
In the case of failure in one device, the others become non-affected.
One of the key advantages is that it reduces the business downtime to a great extent and maintains its smooth operations.
Security
It also makes the process of firewall implementation and handling of access rights much easier with central control.
Decreases the probabilities of improper and intruder’s access to information and the likelihood of hacker attacks.
Performance Optimization
It helps in saving much time and traffic since there is an efficient routing of network.
It greatly reduces cases of collisions of packets in the network hence improving its efficiency in relaying data and information.
This makes Star Topology to be a perfect solution to FP as it offers it a secure (Zubair and Taqi, 2024), reliable and high performance network that can greatly support it in its operations and protect its data.
Network threats are likely to affect FP’s secret information, damage its IT and remain an ever-present threat to the firm’s operations (Xi, 2020). However, the following are three tremendous security threats that FP encounters, followed by their suggested measures:
Unauthorized Access
Threat:
This is because weak authentications could permit hacker to get into the network.
Customer information can be accessed and viewed by wrong hands this is because it is not safe from invasion.
Solution:
Do not allow weak passwords on any accounts and use stringent measures such as use of MFA.
Implement the access control lists (ACLS) so that unauthorised users should not access any resource or information in the network.
Implement the concept of RBAC to constrain the rights of the users so that they cannot perform certain actions or access specific locations within the network.
Malware & Phishing Attacks
Threat:
Cyber criminals use Trojans, viruses, worms and send email automobiles with the aim of cyber phishing.
Also, employees may download files from the internet and access them on the network hence posing a threat to the company’s security.
Solution:
Use firewalls and IDS to avoid any threat that may be produced by hackers.
To protect emails from being attacked by phishing, the company should employ email security filters for this purpose.
Educate employees on measures to take in cases where they receive any phishing and Malware attacks.
Denial-of-Service (DoS) Attacks
Threat:
It involves overwhelming the network with too much traffic and limiting the usage of services offered in the process.
Due to possible changes in business flow, as well as the employees’ interactions with the customers, these changes can happen.
Solution:
To achieve this objective of protecting your system against such traffic, you have to configure your firewall and ACL.
The following should be done to avoid this situation: Employ traffic analysis tools that critically assess traffic in an aim to note several elements of DoS attempts.
There are two options associated with load balancing to balance the network traffic across the different available subsites.
If FP deploys ACLs, VLAN segregation, and intelligent security polices, it can minimize the cases of hacking and other security threats within its network.
To protect a network, one has to start with a proper arrangement of the system hardware. The Future Project (FP) network topology comprises of two routers Cisco 2901, two switches Cisco 2960 and two PCs where testing and implementation were performed (Pavlidis, 2020). These are set in Cisco Packet Tracer to increase performance, security, network and accessibility.
Task 1: Setting Up a Basic Network Topology

Figure 1: Setting the Network Topology
3.1.1 Device Selection and Justification
Facilitates packet forwarding between networks.
Has Access Control Lists (ACLs) for limiting the access to the libraries.
Having introduced the role of firewalls, it means that networks security is achieved through this program.
Task 3: Configuring Routers
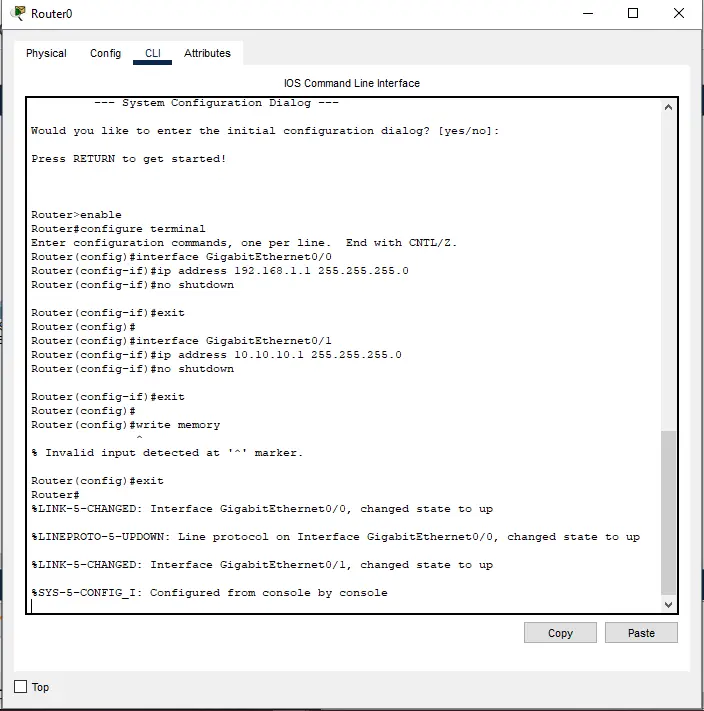
Figure 2: Router 1 Configuration
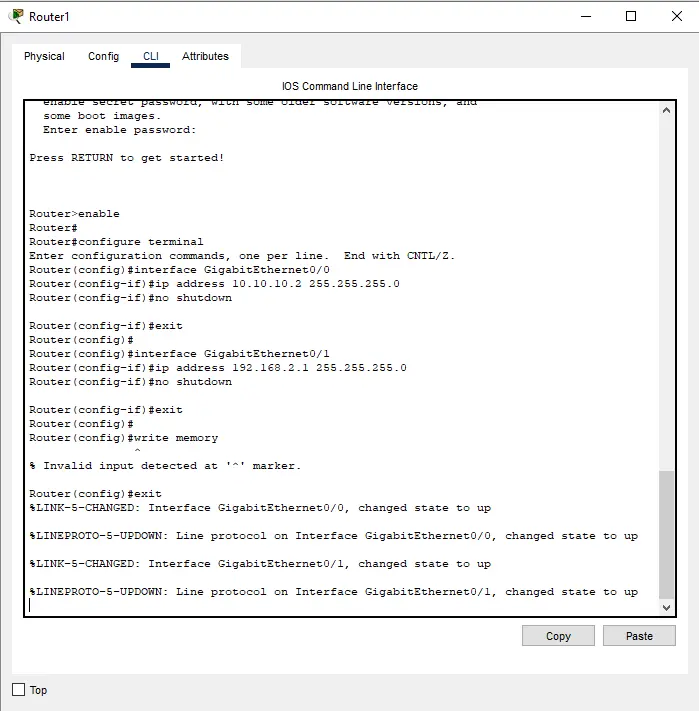
Figure 3 : Router 2 Configuration
Enables LAN communication between devices.
Supports VLAN segmentation to enhance security.
Manages network traffic efficiently to reduce congestion.
Task 2: Assigning IP Addresses and Subnet Masks
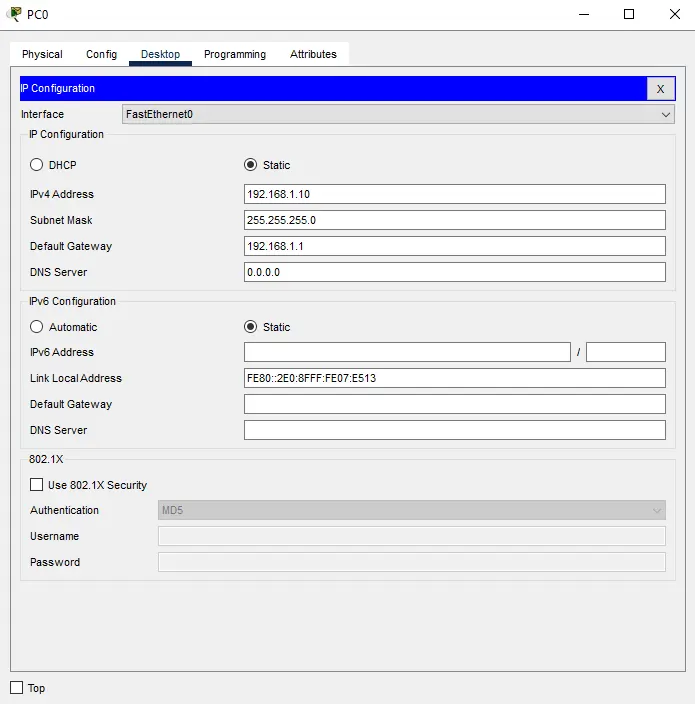
Figure 4: Pc1 IP address configuration
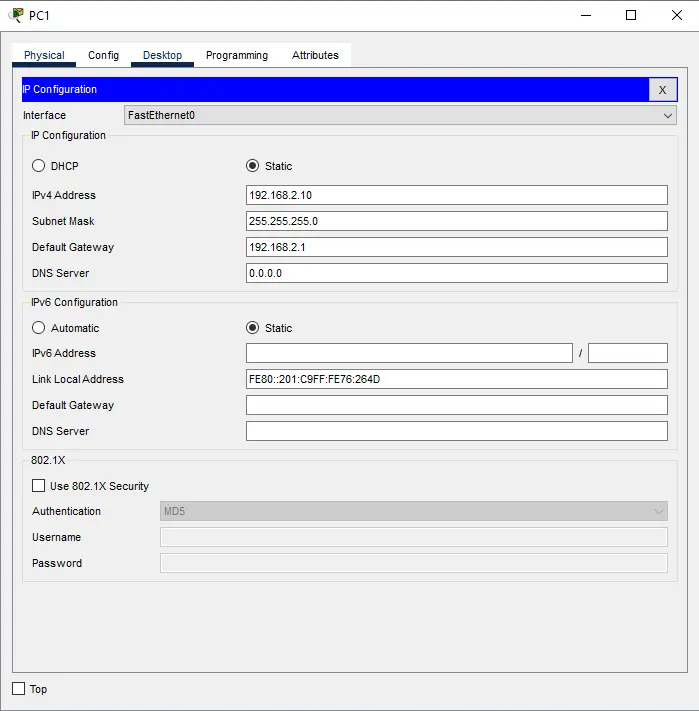
Figure 5: Pc2 IP address configuration
Actively use end-users’ devices for the connection tests.
Ping and ACL are two types of security validations which should be run.
This remains mainly because of the network layout that allows proper communication of the devices while at the same time maintaining high security against cyber criminals.
Routers therefore play a central role in matters to do with security of a network (Lei, 2020). It also becomes possible for an attacker to access configuration of the router and amend or change routing tables and thus interconnectivity mechanism would be paralyzed.
Task 4: Enabling Routing Between Networks
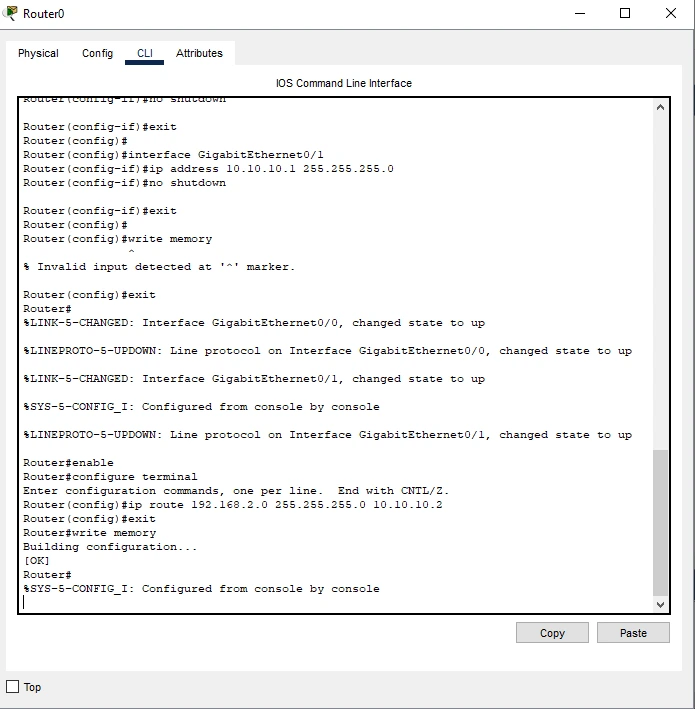
Figure 6 : Configuring Static Routing on Router1
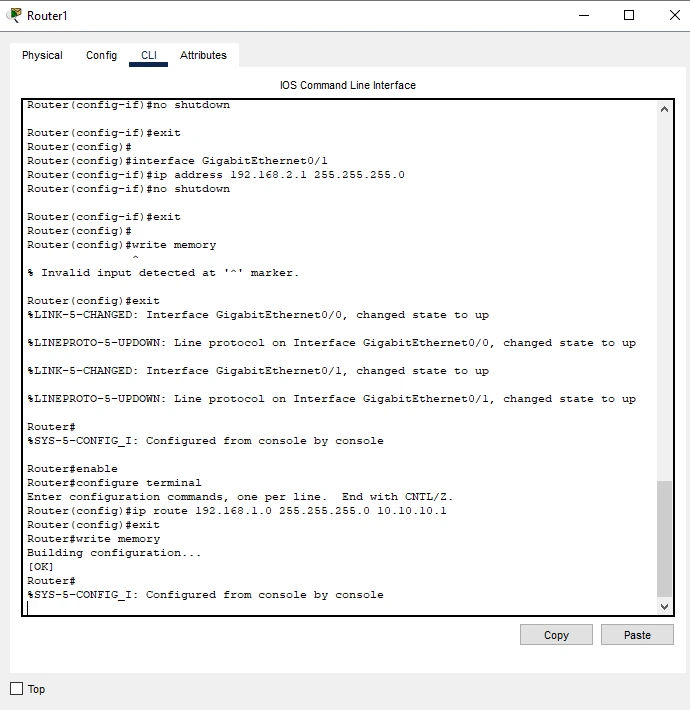
Figure 7 : Configuring Static Routing on Router2
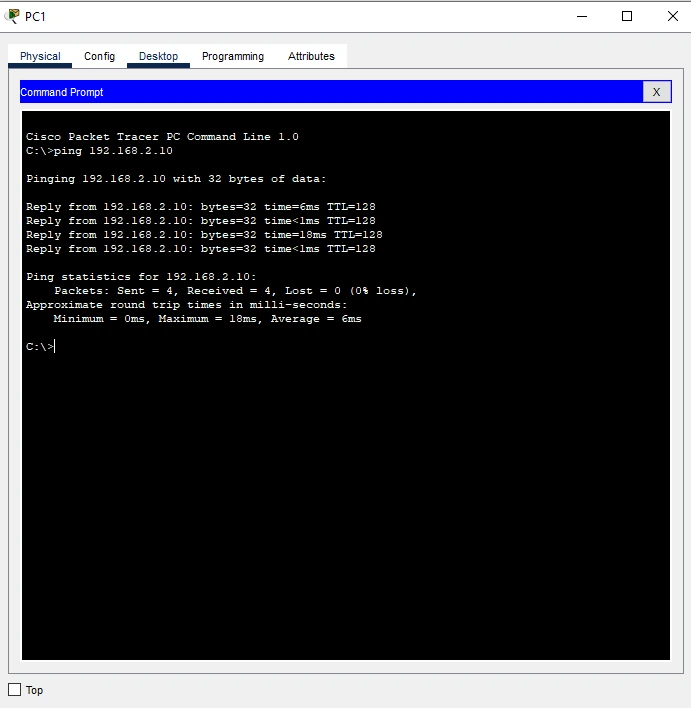
Figure 8 : Testing Network Connectivity
3.2.1 Why Password Security is Important?
Prevents Unauthorized Access:
Enhances the security by preventing the routers from being forced by unauthorized personnel.
Protects Routing Information:
Ensures sensitive configurations remain unaltered.
Encrypts Passwords:
With no encryption used, passwords are held as plain text passwords hence can easily be easily accessed and misused.
3.2.2 Router Security Best Practices
This ensures that there is secure password on routers in the FP thus minimizing the chances of intruder to access and alter the network configurations.
Specifically, Access Control Lists (ACLs) are actually firewalls that dictate which devices and users may or may not enter the network (Frank, 2020). Their major importance is to control traffic, improve security status and prevent access to some valuable information.
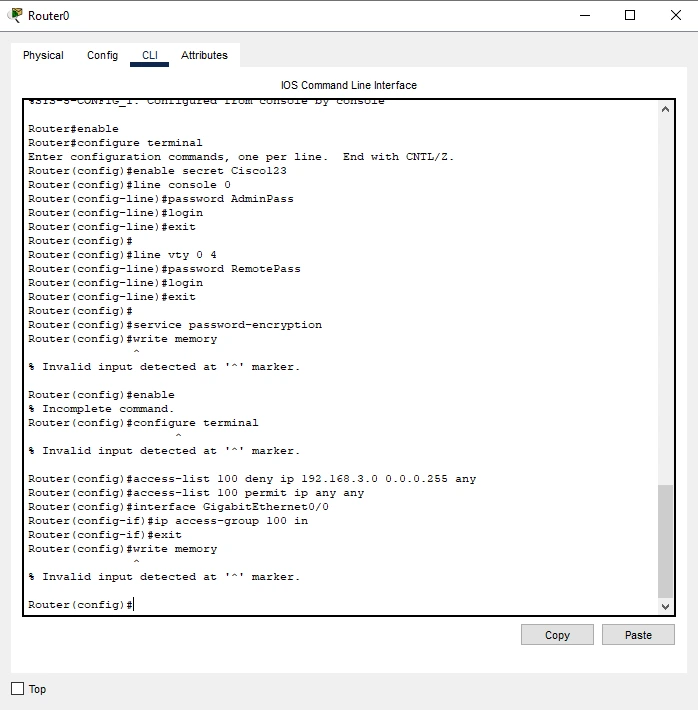
Figure: Configuring Access Control List (ACL) for Router 1
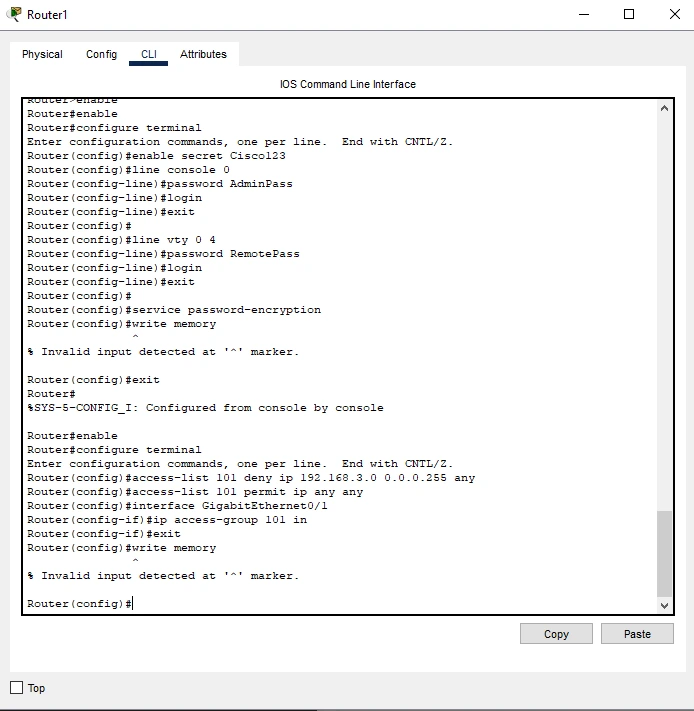
Configuring Access Control List (ACL) for Router 2
3.3.1 Why Are ACLs Necessary?
Block Unauthorized Devices:
Secures computer systems against hacker and unauthorized worker invasion to sensitive computer systems.
Reduce Malware & Cyber Threats:
It prevents the diseases from infecting other equipments within the network since infected equipments are blocked from the network.
Control Network Traffic Flow:
Creates a mechanism that only allows the legitimate users or the specified system services access to the resources.
3.3.2 Impact of ACLs
Thus, ACLs have made it possible for FP to achieve two significant goals ofmaking access to certain systems rare while permitting only allowed network traffic only.
VLANs continue to be physical interfaces of the ongoing building that segregates devices into several network sections making them rather secure and less crowded.
3.4.1 Why VLANs?
Enhances Security
Restricts access between the different departments as to avoid access to information that they are not supposed to access.
Reduces Network Congestion
Reduces the number of broadcasts hence optimizes the traffic in the network.
Improves Management
The security policy can be implemented to the network by controlling the VLANs assigned to different administrators.
3.4.2 VLAN Segmentation in FP Network
Department A (192.168.1.0/24) → Internal Staff Only
Department B (192.168.2.0/24) → Guest Network
The VLAN offers protection to ensure that FP data is not intermingled with other networks lower on the security scale in order to avoid leaking of confidential information.
Once routers, ACLs, VLANs were configured , final test was done and the network was tested and all irregularities were corrected.
3.5.1 Testing Methods
Mainly used in checking the connectivity on the network between the various devices.
Determines whether ACLs are denying or permitting the traffic that is supposed to be allowed.
Displays active routes within the network.
This defines the proper pathways that should be followed by data.
Tests firewall and ACL configurations.
It finds the weak points when the testing is done before the use of the product in real life situations.
3.5.2 Troubleshooting Approach
Checking ACL Rules
This will make sure only the particular devices are allowed to send and receive the signal.
Verifying VLAN Settings
Ensures that traffic is properly separated on the basis of its nature and the department it belongs to.
In this way, FP managed to strengthen its network through extensive testing, provided the highest level of security to its organization, and guarantee IT reliability in case of adverse scenarios.
MAC Address Filtering and Configuration Verification
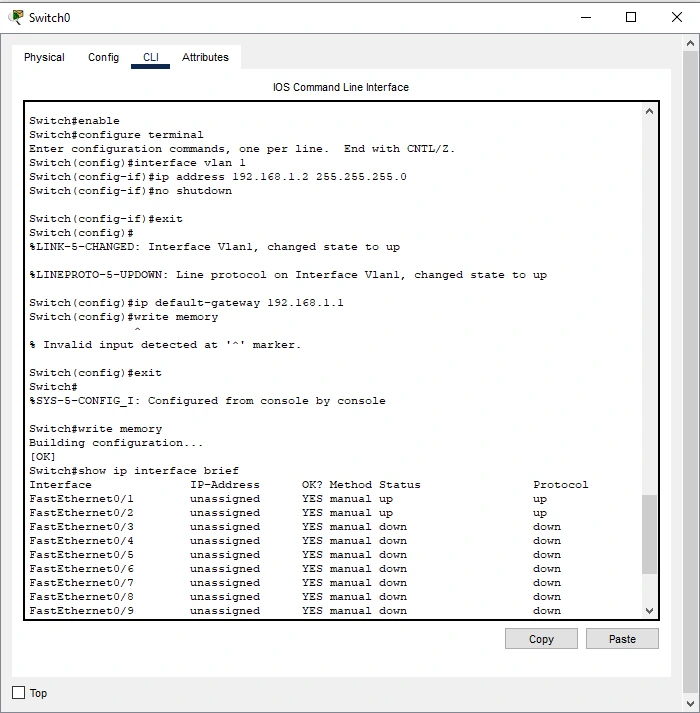
Figure: Enabling MAC Address Filtering for Switch 1
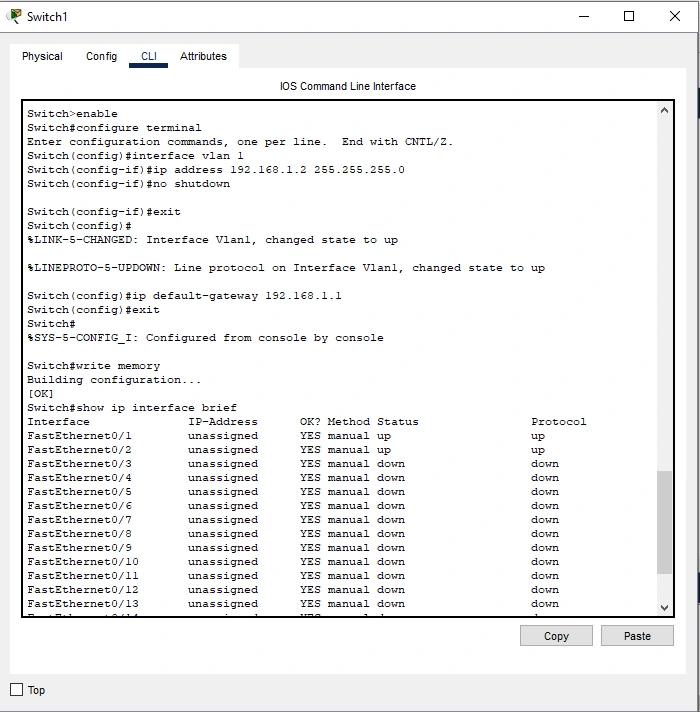
Figure: Enabling MAC Address Filtering for Switch 2
MAC Address Filtering allows a limited number of only authorized devices to access the network, with the result of unauthorized access disallowed. It provides increased security and control on the devices.
Verifying setup, configuration command operations like show running-config and show ip route assure correct routing and security settings are in effect. Ping checks affirm successful exchange of information.
OSI stands for Open Systems Interconnection and it is a framework with seven layers designed to describe how data is transmitted between networks (Považan, n.d.) . It offers a wide scale of recommendations to implement security at different stages of networking hierarchy (Jimenez et al., 2021). In OSI model, each layer is described best security measures that should be implemented for effective protection of the network system, thus beneficial in Future Project (FP).
4.1.1 OSI Model and Security Implementation
|
Layer |
Security Measure |
|
Application (Layer 7) |
Use firewalls & encryption (TLS/SSL) to protect applications from cyber threats. |
|
Presentation (Layer 6) |
Implement data encryption to ensure that transmitted information remains confidential. |
|
Session (Layer 5) |
Use session timeouts to prevent unauthorized access after prolonged inactivity. |
|
Transport (Layer 4) |
Secure TCP/UDP traffic with Transport Layer Security (TLS) and port filtering. |
|
Network (Layer 3) |
Implement firewalls & ACLs to restrict traffic from unauthorized sources. |
|
Data Link (Layer 2) |
Use MAC filtering & VLANs to segment traffic and prevent unauthorized access. |
|
Physical (Layer 1) |
Secure physical access to network devices to prevent unauthorized tampering. |
4.1.2 OSI Model in FP Network Security Implementation
Application Layer Security (Layer 7)
The Application Layer is always involved with the users and applications such as the browser application and mail application and cloud application. (Lei et al., 2020)In the case of security measures in FP’s networks, firewalls are adopted while TLS/SSL for proper encryption.
Presentation Layer Security (Layer 6)
This layer will simply manage the formatting of the data that is to be transmitted. This layer entails security of the pertinent data from the customer by encryption, to prevent it from being intercepted by unauthorized individuals (Santos et al., 2023). AES and SSL/TLS are used in FP for security purposes to ensure confidentiality of information.
Session Layer Security (Layer 5)
This layer focuses on controlling the session between devices connected in a network. session control has also been incorporated in the means thereof to prevent remote login and authentication processes if a session is idle.
Transport Layer Security (Layer 4)
The Transport Layer is concerned with the logical point-to-point data transfer and the maintaining the integrity of data during transfer (Gentile et al., 2024). FP has employed the Transport Layer Security (TLS) and Secure Socket Layer (SSL) as its protocols for the data transfer (Abood et al., 2024). Also, a number of technology barriers are used to block the access of TCP/UDP ports to avoid the direct running of unauthorized network services.
Network Layer Security (Layer 3)
The functions of the Network Layer are routing and forwarding of packets. FP also employs firewalls and Attempt Control List to control the flow of traffic inbound and outbound (Garvik, Lindås and Bø Svendsen, 2023). The ACL restrictions prevent unauthorized IP addresses from accessing the network leaving the gadget’s connection accessible just to authorized devices.
Data Link Layer Security (Layer 2)
The data link layer is responsible for transmitting the data and also check whether the data has reached the intended device without errors (Uddin and Kumar, 2023). MAC address filtering and VLAN segmentation are used by FP to protect this layer from non-authorized access to the data traffic.
Physical Layer Security (Layer 1)
At the fanny of the model is the Physical layer which focuses on ironware credentials in an entanglement Ramprasath and Seethalakshmi, 2021 . FP had limited real real encounter finished constrictive measures such as; locked estimator servers, biometric credentials clearance,' CCTV among others to declaration unauthorized approach to live structures.
When each layer in the OSI model is secured,' it is voltage to protect an organization’s networks and its data as practiced by FP.
The Transmission Control Protocol/Internet Protocol TCP/IP model is the basis of cyberspace communication, ensuring fix data transmittance over networks. It is a four layer model,' each with well defined credentials requirements (Krishna et al.,' 2023). In FP’s network, TCP/IP credentials measures was implemented to preserve unauthorized access, protect data,' and check unquestionable connectivity.
4.2.1 TCP/IP Model and Security Implementation
Application Layer Security
The Application Layer in TCP/IP is in some way equal to OSI’s top three layers, the Application layer, the Presentation layer and the Session layer. This site utilizes commercialized measures such as Secure Sockets Layer SSL and Transport Layer Security TLS to preserve the unauthorized approach to customers’ information. Firewalls was used in estimator systems to declaration or eliminated approach to undesired transaction in web applications.
Transport Layer Security
The fourthly layer of TCP/IP model is the Transport Layer, which provides end to end communications and error control. To fix this layer as well as FP uses TLS, SSL, and TCP/UDP port filtering to deny the effectiveness threats approach to the layer. Intrusion Detection Systems IDS that works at the bear level and could observation some irregularities in TCP traffic.
Internet Layer Security
Internet Layer is the layer that handles an organization’s destination and its routing.
This layer is protected under firewalls, intrusion prevention systems (IPS) as well as IP address control list (ACL) to filter out illegitimate network addresses.
NAT is employed so that an attacker cannot discover internal IPs since they cannot be accessed from the internet side.
Network Access Layer Security
The Presentation, Communication, and Management Layer is an optional layer; and the Network Access Layer is equal to OSI’s Data Link and Physical Layers and is accountable for secure network connections.
FP had Standard VPN as a mode of access for a secure remote connection.
The MAC filtering and VLAN Form of work prevent unauthorized devices from connecting to the network.
4.2.2 Routing Security in FP Network
As a security measure in FP’s network to enhance flow of data; Routing Security is used. These include:
Access Control Lists (ACLs)
Performs the tasks of filtering the traffic that enters and exits the network.
Restricts employee access to only internal-local IPs and any restricted ones defined by the business.
Firewall Implementation
Secures the external interfaces by filtering on the boundary routers, and thus prevent attacks from outside this layer.
Intrusion Prevention Systems (IPS)
He further noted that the proposed system is capable of detecting and preventing any activity before it infiltrates the network.
Network Address Translation (NAT)
Hides internal IP addresses so that the external invasive party will not identify the network devices.
VPN Implementation
Helps keep the remote employees as well as other entities connected in a way that is protected from intrusion.
4.2.3 Importance of Secure Routing
Prevents Man-in-the-Middle (MITM) Attacks
This makes it impossible for the attackers to breech into the communication line and get hold of sensitive information due to encryption.
Ensures Data Integrity and Confidentiality
Both OSPF and EIGRP have been encoded with certain measures to ensure security during transmission of data.
Reduces Cyber Threats
In particular, the measures that have been taken by FP in controlling cyber threats include firewalls, ACLs, VPNs so as to minimize the disruptions of the business.
|
Feature |
OSI Model |
TCP/IP Model |
|
Number of Layers |
7 Layers |
4 Layers |
|
Security Implementation |
Security is applied at each layer separately |
Security is integrated across fewer layers |
|
Application Security |
Uses firewalls, encryption, and session management |
Implements TLS, SSL, and VPN security |
|
Transport Layer Security |
Encrypts TCP/UDP traffic |
Uses TCP/UDP security to prevent unauthorized access |
|
Internet Layer Security |
Uses firewalls and ACLs for IP security |
Uses firewalls, IPS, and NAT to protect routing |
|
Network Access Layer Security |
Uses VLANs and MAC filtering |
Implements VPNs and secure wireless communication |
The OSI and TCP/IP models will act as useful tools for applying reliable security measures in the network that is used in FP (Anwar, Abdullah and Pastore, 2021). Implementing encryptions, firewalls, access control lists (ACLs), virtual private networks (VPNs), and intrusion detection systems (IDS) in both models contribute to developing the strong safety and productivity of networks for FP.
With each layer of communication being secured, FP ensures customers’ data and information security from cyber criminals; and provides a secure, flexible, efficient, customer-oriented networking system.
Describes the appropriate employee conduct and behavior in the context of the Internet and BYOD policies.
This is due to the restriction of the web accesses that are deemed to be suspicious with its aim of blocking phishing attacks.
Limits administrative privileges to authorized personnel.
Uses RBAC to control flows for access restriction.
5.3 Incident Response Plan
Step 1: Detect security breach.
Step 2: Limit and quarantine the spread of the virus to the affected systems.
Step three thus involves wiping out the threat and patching up the holes:
The fourth step is to restore the lost data and entice regular operations back into life.
Post-Incident Analysis An effective response to a security threat must follow an analytical procedure designed to require post-incident analysis to prevent future security breach.
6. Conclusion
This paper has highlighted network security measures of Future Project (FP) including routers, access control list, virtual local area networks and OSI/TCP. This way of working guarantees that FP’s network is protected against all cyber threats and operates at a high level.
Key Takeaways:
That is why router password protection is used to ensure that other people do not connect to the system.
Access Control Lists (ACLs) help a lot in the process of denying access to the network traffic which is not required.
It also makes the organisation of the networks much easier because VLAN segmentation enhances the efficiency of networks.
Since OSI and TCP/IP models are important in the implementation of a network, the two are essentials in the defense of a network setting.
Future Recommendations:
Implement Intrusion Detection Systems (IDS).
Provide virtual private network facility for computer networking over the internet.
Conduct the security audit exercise frequently so that weaknesses in the security system are easily identified.
Such measures can give very good results as FP will be able to uphold data security, networks and business continuity in the future.
Reference List
Journals
Introduction Professional development in healthcare is principally founded on reflective practice where professional...View and Download
Introduction to Principles Of Financial Planning Assignment Based on these financial concerns and objectives, I have provided...View and Download
Task 1- Organisational Behaviour Assignment This focuses on organisational behaviour assignment, which is really the study of...View and Download
Introduction to Organizational Behavior in Corporate Assignment Because of the tremendous rise in networking, individuals...View and Download
Introduction: How Dietary Fiber's Impact on Cardiovascular Health Cardiovascular disease or CVD is the leading reason of death...View and Download
Introduction to Organisational Performance Assignment Sample 1.1 The process of developing Organisational Strategy An...View and Download
